Cybersecurity – An Evolving Threat
Cybersecurity – An Evolving Threat
We were pleased to have cybersecurity expert, Tom Spitnale, AVP for SyCom Technologies, join us for this year’s higher education summit. In his presentation, he provided information on warning signs, tips, and insights into the ever-changing topic.
Cybersecurity has been a hot topic in different iterations for the last 5-8 years. It’s no longer something you plan and then deploy, it’s an investment you make throughout your entire institution from both a technology and personnel standpoint.
Your Priorities
When it comes to cybersecurity, you should orient your priorities around the CIA Triad, and no, this doesn’t mean the Central Intelligence Agency. All institutions have concerns over the Confidentiality, Integrity, and Availability (CIA) of critical information technology assets. It boils down to three important questions: is the information confidential to me, available to me when I need it and when I get to it, can I trust it? All of these things are the foundation of what drives cybersecurity initiatives. Although all are important to everyone, they are uniquely important to individual organizations based on their priorities and their initiatives. So setting priorities for your institution is extremely important in driving your cybersecurity initiatives.
What is the Cost of a Breach?
While the average cost per record lost or stolen is $141, the overall cost includes other direct and indirect costs associated with the breach.
Direct Costs
Detection & Escalation
Forensic Investigation
Remediation
Post System Implementation
Compliance Costs & Fines
Incident Response Rates as high as $900+ per Hour
Indirect Costs
Down Time
Notification Costs
Public Relations
Legal Expenses
Product Discounts
Customer Churn
The root cause of breaches can be broken down into three buckets: malicious or criminal attack (47%), system glitch (25%), and human error (28%).
Next Steps
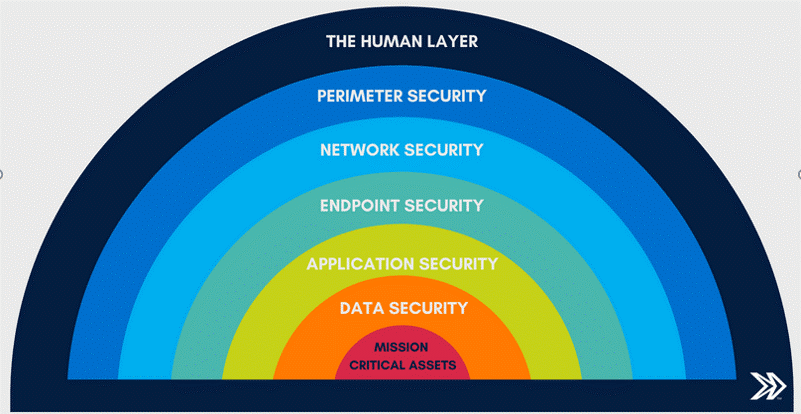
The good news is, that there are steps you can take to minimize your institution’s risk against breaches. The riskiest part of the solution is always the people. This can mean awareness training, particularly around phishing, and investing in tools that help you identify phishing attacks. Consider your data as your mission-critical assets, then everything that you layer on top is your security layers.
Your organization may or may not have had a security breach but regardless, every investment into cybersecurity is a reaction to an incident or a fear of an incident. The reaction generally takes two forms, people-centric or technology-centric. The people-centric response involves creating and enforcing clear policies, and providing HR and risk training, and practice. Technology-centric responses include planning, deployment, and standardized patch management and maintenance. These responses are a continuous loop of evaluating, investing, training, deploying, and re-evaluating, and that is the world we all live in.
The Brown Edwards team has experience in cybersecurity including incident response planning, IT security and vulnerability assessments, and penetration testing. Contact our team today to see how we may be able to assist your institution.

%203-Jul-21-2022-01-55-44-27-PM.jpg)
